Hash-based Message Authentication Code (HMAC)
Availability: on request
HMAC authentication creates a cryptographic signature of the request body that can be verified by the webhook server. This is a common pattern in webhook authentication to ensure the integrity and authenticity of the webhook payload, the tradeoff is a slighter more complex authentication method to implement.
The webhook server will independently create the hmac with the same secret key and request body, and if the signatures match, it confirms that:
- The request body hasn't been tampered with.
- The request came from someone who knows the secret key.
const clientSecret = 'T6Q3Y1VXNB';
const requestBody = {
"request_token": "480aae3a-a850-4276-b3a2-e8698988e016",
"timestamp": 1749218054258,
"type": "create:evaluations:run_create",
"description": "Notify on Creating an Evaluation Manually",
"data": {
"agent_info": "[email protected]",
"evaluation_token": "L-XFB1N2mw5aSzkQ89W39d",
"application_token": "1hEl73OxaY7cGX1B2pcsOUj8XuVit3Mf",
"entity_token": "P-Vc8WGJJ9Dgqu3Kk73OlX",
"status_code": 201,
"evaluation_status": "complete"
}
};
const hmac = crypto.createHmac('sha256', clientSecret);
hmac.update(JSON.stringify(requestBody));
return hmac.digest('base64');Example Authorization header:
POST /webhook-endpoint
Authorization: Nyftzq+13l9qookC19OKkHdeo/9CWbctcazu4ywWjm4=
Content-Type: application/jsonExample webhook configuration:
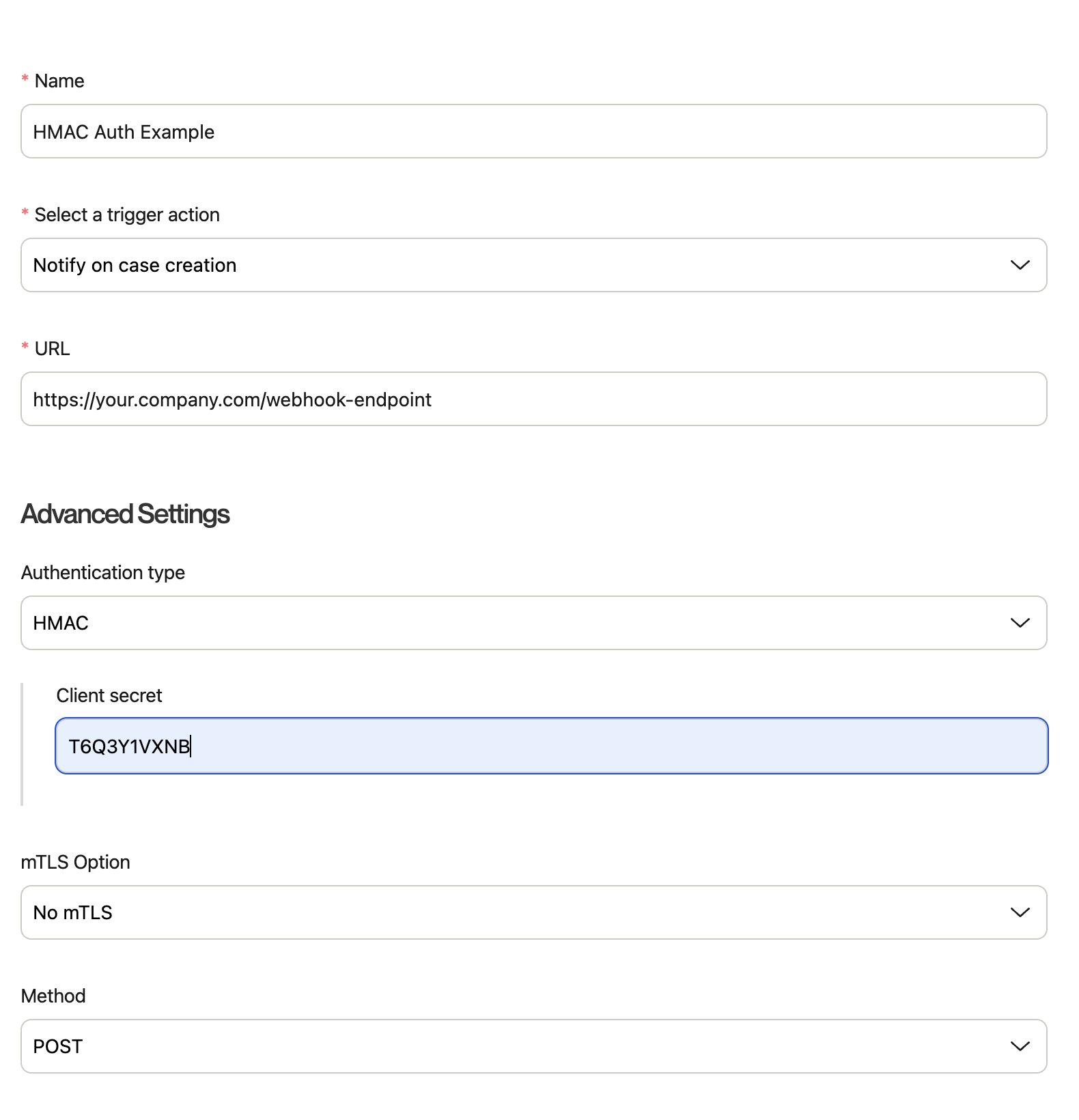
Updated 5 months ago